People - system users
This section can be found under Features—People. Here, you can add people who can log in to the system. You can change their access control type, such as simple user or administrator.
Click newNew on the right-hand side to add a new user/person.
If you use the 
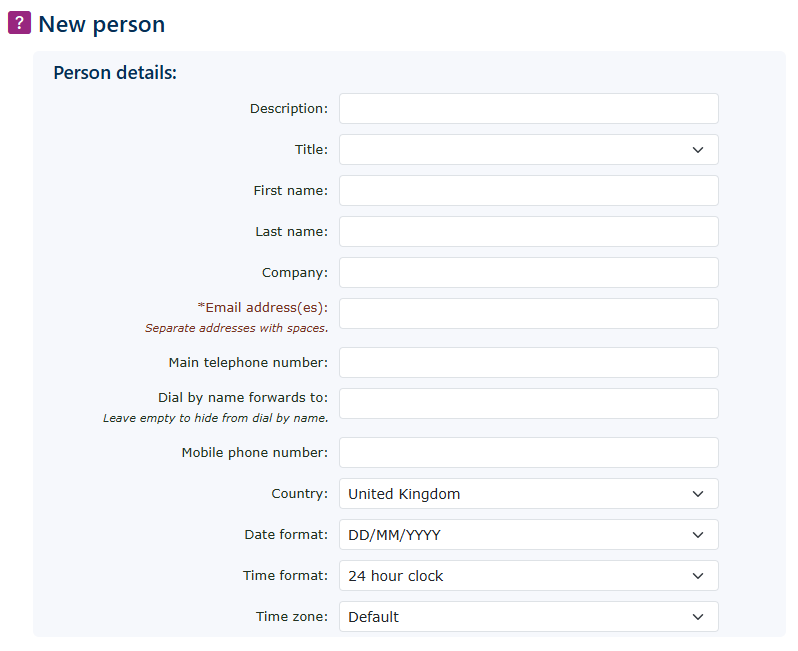
| Description | This is used for information purposes. |
| Title, First name & Last name | This could be used in conjunction with a users extension |
| Company | This is used for information purposes. |
| Email Adress(es) | This must be completed, as it is used for password recovery and voicemail-to-email if the user/person is set as a mailbox owner. |
| Main telephone number: | This is used for information purposes. |
| Dial by name forwards to: Leave empty to hide from dial by name. |
These are the details used if you allow a dial-by-name service to be enabled (i.e. when using an IVR auto attendant function) |
| Mobile Phone Number | Used to provide SMS notifications for VM messages |
| Time format | Used when logged in to the portal to provide the correct format. |
| Date format | Used when logged in to the portal to provide the correct format. |
| Time Zone | Used when logged in to the portal to provide the correct time zone. |
Complete all the boxes as required.
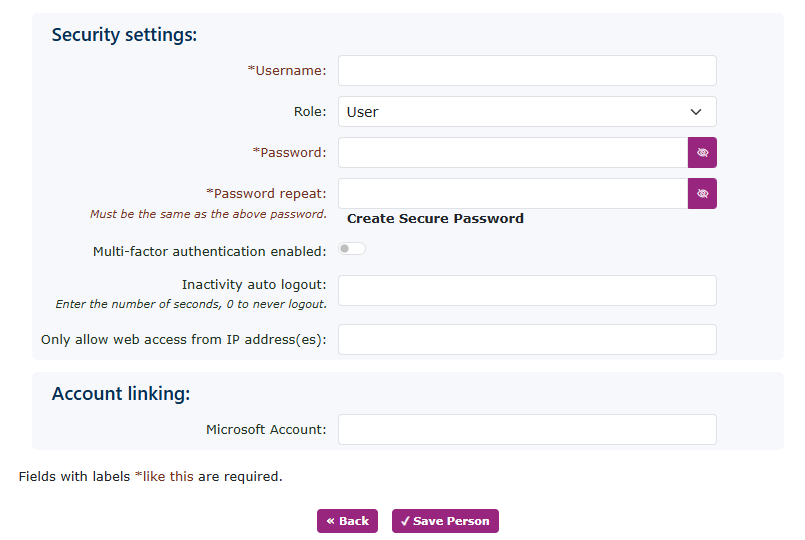
You must complete the mandatory boxes before you can save the new person.
The User name will be used as the portal login name and must be unique. Setting a simple name like John will not be allowed, as there could already be a John on the system. We recommend using the person's email address, which will likely be unique.
This must also be completed as it is used for password recovery and voicemail to email if the user/person is set as a mailbox owner.
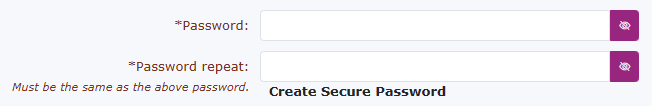
Finally, the password must match and contain at least ten characters. This can be alphanumeric or any special character.
Security
To enhance security and prevent fraud from unauthorised logins, we offer two security methods.
1,
2,
| The second method restricts logins to specific IP addresses. While this can enhance security, it may not be ideal for users who frequently access the portal from mobile devices, as these can utilise multiple IP addresses from the mobile network. This method is most effective when the user's login is confined to a single, dedicated IP address. |